



How to do it, with suggestions for more reading
Today, computers are usually used for encryption and decryption. In other words, when you visit a secure website, the information you send and the information you receive is encrypted so that only you and the other website can see it. If someone tries to tap the line between the two of you, the information won't be understandable.
Of course, it might be possible for someone to see the information in another way. If someone is looking over your shoulder while you visit the secure website, it won't make much difference how well encrypted it was. Or if someone else logs into your computer, they can probably view the information.
In the days before computers, there were methods of sending secure information. The most secure method was called the "one time pad" method. That method is explained on this page, and you will learn how to send and receive messages this way. This method is explained in more detail on Wikipedia.
The method is called the "one time pad" method, because it usually used a pad of paper. Each sheet of paper was filled with random letters. When one sheet was used, it was never used again, hence, the name "one time pad." For the system to work, both the sender of the message and the person receiving it had to have a copy of the same pad. And just as important, nobody else could have a copy of the pad.
It was normally used like this: You need to communicate with your spy in a foreign country. Before he goes, you give him a one-time pad, and you keep an identical copy. He hides the pad and begins his mission. He then waits for your encrypted messages.
Each page of the one-time pad will look something like this:
ONE-TIME PAD KEY NUMBER 1
G X I T Z K M E I V T I B E P 5 D B E P T K J E N
E J O 9 I U I O R E R F E W K B 9 K J E R Q 3 W B
As we will see, because this key is 50 characters long, it can be used for messages that are up to 50 characters long.
Now, it's time to send our agent a secret message. Let's say that our message is:
BLOW UP THE BALL BEARING FACTORY 3 AM TUESDAY
We don't really need the spaces between the words, so we can write it this way:
BLOWUPTHEBALLBEARINGFACTORY3AMTUESDAY
Or, if we wanted to make it easier to read, we could simply put the letter X between all of the words. X is rarely used in English, so that might make it easier to read:
BLOWXUPXTHEXBALLXBEARINGXFACTORYX3XAMXTUESDAY
Because our one-time pad has the letters divided up in groups of five, we divide this message up into groups of five letters. And for this example, we won't worry about putting an X between the words:
B L O W U P T H E B A L L B E A R I N G F A C T O R Y 3 A M T U E S D A Y
Next, we write the message on the one-time pad. In this example, our message is written above the letters printed on the pad:
ONE-TIME PAD KEY NUMBER 1
B L O W U P T H E B A L L B E A R I N G F A C T O
G X I T Z K M E I V T I B E P 5 D B E P T K J E N
R Y 3 A M T U E S D A Y
E J O 9 I U I O R E R F E W K B 9 K J E R Q 3 W B
Next, we need a method to combine the original message and the key into an encrypted message. There are various ways of doing that, but one of the easiest is by using a table such as this one:
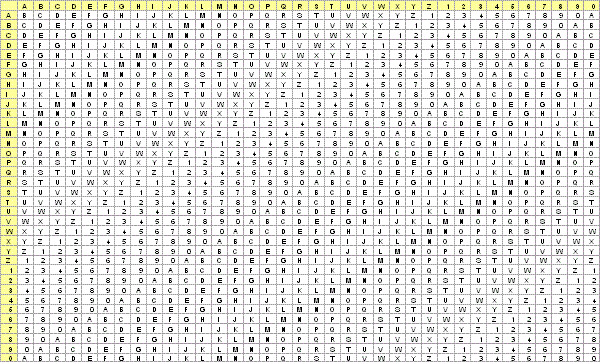
If you would like a better copy of this table, you can download a PDF.
Now, the work becomes a bit tedious, but not particularly difficult. We need to go through the one-time pad, and for each group of letters, we can look on the chart and find the letter that will be used in the message. The letters going up and down the left column are the letters from the original message. The letters going across the top are the letters from the one-time pad. Where the two intersect is the letter to be used in the encrypted message. The first pair of letters are B and G. Therefore, we go down the left to B, and across the top to G. Where they come together is the letter I. So the first letter of the secret message is I, and we write that on the pad below B and G.
The next letter of the message is L, and the letter below that on the pad is X. Again, we go down the left to L, and across the top to X. here they come together is 0. We continue writing these on the pad, and get the following:
ONE-TIME PAD KEY NUMBER 1
B L O W U P T H E B A L L B E A R I N G F A C T O
G X I T Z K M E I V T I B E P 5 D B E P T K J E N
I 0 X G J 1 7 M N X U U N G U 6 V K S W Z L M Y 3
R Y 3 A M T U E S D A Y
E J O 9 I U I O R E R F E W K B 9 K J E R Q 3 W B
W 9 H 0 V E 4 T A I S 5
At this point, we have the encoded message, and we also need to tell our agent which pad to use. So we can send a message something like this: KEY1 I0XGJ 17MNX UUNGU 6VKSW ZLMY3 W9H0V E4TAI S5 The first part of the message tells the agent which pad to use. The rest is the message itself. We can send this message any way we like. We can send it by radio, we can put it in the newspaper, or we can write it on a wall somewhere. Many people might be able to see it, but unless someone else got a copy of the pad, only our agent will be able to understand it.
To do this, our agent goes back to his room. He sees that he needs to use pad number one, so he gets out his copy, and writes down the encrypted message above the letters that are printed there:
ONE-TIME PAD KEY NUMBER 1
I 0 X G J 1 7 M N X U U N G U 6 V K S W Z L M Y 3
G X I T Z K M E I V T I B E P 5 D B E P T K J E N
W 9 H 0 V E 4 T A I S 5
E J O 9 I U I O R E R F E W K B 9 K J E R Q 3 W B
He then reverses the process to decode the message. He remembers that the letters of the key are the ones that go across the top of the paper, so he goes to the letter G. He goes down that column until he gets to the letter I. Remember, the letters in the middle of the chart are always the letters that are in the encrypted message. Then, he goes to the left and sees that this is the row marked B. So the first letter of the message is B, and he writes that down below the I and the G. Then he moves on to the next set of characters, which are the number 0 and the letter X. He goes across the top of the chart to X, and then goes down until he finds 0. He looks to the left of this column and finds the letter L. He continues until the message is all filled in:
ONE-TIME PAD KEY NUMBER 1
I 0 X G J 1 7 M N X U U N G U 6 V K S W Z L M Y 3
G X I T Z K M E I V T I B E P 5 D B E P T K J E N
B L O W U P T H E B A L L B E A R I N G F A C T O
W 9 H 0 V E 4 T A I S 5
E J O 9 I U I O R E R F E W K B 9 K J E R Q 3 W B
R Y 3 A M T U E S D A Y
He now has the full message: BLOWU PTHEB ALLBE ARING FACTO RY3AM TUESD AY. He puts the spaces in the correct spot, and early Tuesday morning, he takes his bomb to the ball bearing factory.
As long as it is done properly, the one-time pad method is mathematically impossible to decipher. But it must be done properly. The one-time pad must truly be random. If there is any pattern to the letters in the pad, then there is always a chance that the enemy's computers can crack the code. And, of course, if the enemy somehow got a copy of the pad, then the code is completely worthless. So the spy needs to be very careful never to let anyone see the pad. And just as important, the spy must burn the pad after it has been used. If the same pad is used a second time, then there will be a pattern that can possibly be cracked.
If the spy is arrested, all of these one-time pads that he has hidden in his room will certainly look suspicious. Therefore, it might be advisable in some cases to use something more innocent looking. It's not as secure, but it is possible to use a book as a one time pad. Again, there is a pattern to the words in a book, so eventually, a strong enough computer will be able to crack the code. But if the spy is operating behind enemy lines, the possession of the one-time pads would be suspicious, and it might be worth the risk to use an innocuous book.
Again, both the sender and the receiver of the message must have identical copies of the book. It turns out our spy is a fan of volcanoes, and he has a copy of the 1909 book "Wonders of the Volcano". His headquarters also has a copy of the book, and they have agreed that they will use this book to encode and decode their messages. When he gets his next message, it begins with "KEY27-1". It has been pre-arranged that this means he will turn to page 27, paragraph 1. He turns to that page, and finds the following:

Using the words printed on this page, he can make his own one-time pad:
HOMEMADE ONE-TIME PAD FROM PAGE 27, PARAGRAPH 1 A N D C O N S I S T O F E N T I R E B A N K S O F S U L P H U R O F A D E L I C A T E A N D B E A U
At this point, the process is done the same way as with the one-time pad that the spy brought from headquarters. Headquarters encrypts the message using this pad, and the spy decrypts it in the same way. Again, given sufficient computing power, this code can be broken, especially if the enemy suspects which book it might be. But in most cases, this method is very secure.
If you're interested in learning more about codes and ciphers, you will find many of the following books interesting. You can find them at your library, or order them online from the following links:
If you're interested in recreating an old copying and duplicating method, please visit my
hectograph page.
Return to my main page.
Please support this page by supporting our advertisers by using the following links:

©2013 W0IS.com
Return to my main page
Copyright and privacy policy